
In the olden times, people recommended writing down your passwords. As a traveler, carrying around a book full of passwords is not a good idea: what if you need them while you’re out, or what if you lose it?
Scenario 1: Losing Your Devices
Keeping your passwords exclusively on any one device is also not a particularly good idea: what if you lose your computer or your phone, or both?
Really, think about it, how would you get all your accounts back?
Your answer to this may have been “well I’ll just log into my email and use the ‘reset password’ function everywhere” – but what if you left it logged in on the device you lost, and whoever either finds your device or hacks you, also logs into your email, and changes your password and recovery details on it?
Then what?
Scenario 2: Needing Your Passwords While On-the-Go
Having my passwords at-hand while on-the-go (i.e. on my mobile devices) has saved me multiple times, both personally and professionally.
Imagine this: some emergency comes up, and all you need to do is login somewhere and flip a switch, or move some money, but you’re the only one with the account details, and you’re 4 hours from home.
What do you do?
Reactively, you could either:
Like What You See?
(a) accept the ramifications and let it wait until it’s convenient for you,
(b) rush back and burn your plans for the day while still taking a loss (of some sort or another), or
(c) hope against hope that there is some relevant support infrastructure available that can authenticate you without your key account details
(and all this is assuming it’s a simple “flick of a switch” to solve – often it isn’t).
Preparation Is Key
While it’s crucial to remove single points of failure that could result in those kinds of situations, they’re bound to happen sooner or later in some form another, and so it’s important to be able to access your accounts wherever you are, both in case of emergency, and for the added day-to-day convenience of having access to your digital life.
Even more important, is to make sure that those passwords are safe, no matter where you are.
The first thing I am presuming here is that you use secure passwords. If you’re not using long, strong passwords, and you’re not making a new password for everything you have to log into, then you’re probably using the same, weak, easy to remember password for everything, and you don’t need to store them anywhere. You also have other things to worry about than just your devices being stolen or lost; don’t be surprised when one day, after signing up to the wrong site, every account you have gets hacked into simultaneously.
Strong passwords are important. An easy way to evaluate yours, is that if you can remember your passwords (or if they look anything like this, or this, or this, or.. you get the point – hopefully), they’re neither strong enough, nor varied enough – i.e. you’re using weak passwords and/or the same password again and again.

via xkcd (click for full version)
If you’re making passwords so secure that you can’t remember them, you’ll need a place to store them.
Enter, Password Storage Solutions
To protect from the multiple eventualities in which you could irrevocably lose access to most if not all of your accounts – you’ll want to make sure that the solution you adopt fits 3 key criteria. If it doesn’t, encountering even one of those eventualities may relegate a (perhaps short, perhaps prolonged) period of your life to long days and nights of emails, phone calls, and sending your IDs/address proofs to the handful of services/website/companies which you would stand even a chance of recovering – let alone the time it would take for you to repair the damaged caused by weeks if not months of the inability to access your accounts.
The storage and use of strong passwords is important, and therefore, so are the criteria that define what makes a good password storage app:
Criteria
Cross-Platform:
First of all, you have accounts that you use across your devices, via Apps/programs, and websites. The right password management solution will allow you easy access across all your devices. Within the devices themselves, it should be convenient to access your passwords for use across multiple apps (e.g. not just easy to use for websites, but also on other apps). At the very least, quick copying and pasting from an App across all your devices – additional points for the more auto-filling it can do (e.g. for websites across multiple browsers, and within other apps/programs themselves).
Cloud-Based:
By having your password management solution in the cloud (“cloud” basically means “stored on other peoples’ (usually companies’) computers”), you get two key benefits. Firstly, it’s a convenient way of automatically synchronizing (read: being able to access) the passwords across multiple devices, which doesn’t rely on them being close to each other to get the latest password (as would be the case with, for example, Bluetooth, NFC, or LAN). Secondly, if you happen to lose all your devices, your passwords will still be “stored” somewhere remote, where you can recover them all together. This does bring up the important question of: “well who am I storing my passwords with, and what exactly is being stored?” Which is also the reason that “stored” was in quotes, and will be addressed separately for each of the solutions.
Closed-Access:
Given that the password management solution will store its data in the cloud, and be accessible across multiple devices, you have to have a secure way to access your passwords. What’s more, is that you should be the only person to be able to do so. That means, it shouldn’t be easy for another party to access your passwords, or log in to your accounts – even if they get access to your device (whether by hacking, loss, or theft).
Let’s get into the 3 major types of password storage/management options, see how they stack up against each other based on our criteria, and find the top recommended options:
Type 1: Browser-Based Password Storage
This is the way that most people store their passwords, because it’s “what’s there”. Browser-based password storage has revolutionized the password-storing habits of the masses, and it’s certainly better than having the same password everywhere, but let’s see how it stacks up as a solution for secure password management:
Cross-Platform:
The answer is in the name: browser-based. There are several inherent drawbacks:
– It’s only convenient if you use that browser, so if the website you’re on doesn’t work well with that browser, your password isn’t quickly accessible.
– Browsers are used to access websites, so just like the inconvenience of accessing your passwords via another browser-app, it’s inconvenient to access them for use in another App-app.
Cloud-Based:
Browser-based password storage can be stored in the cloud, but it depends on the browser’s capability to do so. The more popular ones, Chrome, Firefox, Opera, and Safari all do this, but only Safari (which doesn’t work on Android or Windows) does it automatically via Apple ID (and you have to set it up first).
For the other browsers, you’ll have to sign in to another browser-specific account, which also syncs other things besides your passwords. While some of those can be useful (e.g. bookmarks), there are also other cases where you may not want your browsing data to be synchronized/tracked across multiple devices.
This brings up the question of who is storing your passwords? Well, in the case of browsers, it’s the company or organization that manages the browser. For the major browsers, that is:
Chrome: Google
Safari: Apple
Firefox: Mozilla
Opera: Formerly Opera (Norway), Now Otello (owned by Chinese investors)
In terms of the first two, you probably are already sharing sensitive data with them, and both Google and Apple are big enough companies that we know:
(a) They have the resources to fight and preemptively protect themselves against breaches
(b) They have the resources and intention to be around for a long time
The third, Mozilla undoubtedly dramatically changed the “browser game” forever, as FireFox was a ground-breaking browser. They are a very well-respected organization, but they say themselves that their password sync service isn’t to be relied on. While their recommendation to keep backups is perhaps just as much a legal disclaimer as it is good common practice, it none-the-less contains the same message: we are not your password storage service.
And as for the fourth, Opera (now Otello), it was originally a Norwegian company, until it was sold to a Chinese group, who changed its company name to Otello, which was a logo that looks eerily like somebody spying on you through a pair of binoculars. While it’s a public Norwegian company listed on the Oslo Stock Exchange (OSE: OTELLO), that logo, combined with the legendary Chinese predisposition towards spying (and in recent news, even creepier things), is enough to make me keep my passwords as far away from Otello & Friends as possible. (? O, tell-o me all your secrets ?)
Additionally, it’s important to know that none of the browser-based cross-device synchronization is enabled by default – for example, if you have Google Chrome on your computer and your phone, they won’t synchronize unless you set it up – so you’ll have to manually setup synchronization, which is something that many people may overlook until it’s too late.
Closed-Access:
Part of the convenience of using browser-based password storage is that you can be automatically logged in to sites, or at least have your detailed pre-filled for you. But, browsers are very trusting things, and they don’t differentiate as to who it is that’s doing the browsing. If somebody gains access to your device, they can log in to all the websites you have saved passwords for. Additionally, they can go into the password storage section of your browser, and unlock all your passwords (presuming they already got into your device and know your device’s password).
Firefox is the only one of the major browsers that has its own “master password” that would thwart such people from actually seeing your passwords, but not from logging in to your accounts, where they could then change your passwords. On top of that, using a master password in Firefox disables password synchronization, so if you enable the added security, you can no longer use it across your devices.
I would give this a negative if I could, it’s so bad. But this is my rating system after all, so let’s say this one is actually negative one kajillion.
Overall:
(Or, if you’re keeping track, approximately negative one kajillion. Don’t rely on browser-based password storage.)
Type 2: Password Manager
What do you get when you take the majority of the functionality of browser-based password storage, add some extra bells and whistles, then bundle it up into its own separate application?
A password manager.
In some sense the “next step up” from browser-based password storage, password manager apps let you store all your passwords in one centralized location, and by virtue of having the apps installed across all your devices, give you access to those passwords wherever you are.
They work across multiple browsers (even if they require plugins/addons/extensions for each browser), and thus free you up from being constrained to any one browser for easy password retrieval.
There are multiple password management apps available. First, we’ll get into them generally (as a concept), and then talk about specific apps.
Let’s see how they stack up against our criteria.
Cross-Platform:
In terms of “coverage” across multiple platforms, password managers do it best.
On your computer, they integrate into your browsers, and can also have their own separate App.
On your phone, they can integrate with the top browsers, many apps on iOS (actually, pretty much all apps since iOS 12), and most apps on Android. Then, if there is an issue with automatic logging in, they also have their own separate App, in which you can easily search for, find, then copy and paste into whatever app or website you need.
It doesn’t get much easier than that. (Although it could, slightly, if more apps were supported, but for the moment they are the best mass-market solution in terms of convenience across devices, and with the improvements in iOS 12, pretty much all apps are supported on iDevices).
Like What You See?
Cloud-Based:
Password managers score higher than browsers in the cloud-based category, despite many similarities.
Firstly, naturally, you also still have to log in and setup the password synchronization across your devices, although that is made explicit and very obvious in this case. You have to install the app, and the app will ask you to log in. No confusion there, no assumptions to be made about being logged in but not actually having your passwords available everywhere.
Next, the passwords are “stored” with a third-party company – the companies that make the respective password management apps. They’re very much “in the cloud”, since they sync across your devices as one of their primary purposes.
“Stored” is in quotation marks above, because although the third-party company acts as an intermediary, they don’t store your actual passwords, just a hard-to-decipher representation of them called a “hash”. You can think of it like a secret code that is made uniquely for you, out of a much, much more complicated version of “every letter is actually 3 letters before it in the alphabet, so D = A”.
Of course, that’s if you believe them.
Although password managers are very much the most convenient option, they are also a potential target for hackers, and they are not impenetrable.
Hacking is very big business, and the bigger the target, the more collective money and time goes into getting in.
Compared to Apple and Google, which are themselves not invulnerable, small companies like the ones that manage password storages don’t have nearly as many resources to devote to securing their operations. This is not to say any one particular company is more or less vulnerable than the others (nor speculating about their earnings and the resources at their disposal), just that as a generalization, they are potentially big targets without big budgets.
This is part of the reason that the larger of the password manager companies use hashing to store the passwords: if not even they can access the data, then it’s harder for hackers to do so (but not impossible) – and therefore, by adopting a data storage model whose motto is “there’s no treasure here!“, they become a smaller (albeit still visible) target.
The size of these companies brings another worry to mind, and perhaps one that is more pertinent and practical: where will they be 5-10-15 years from now? How many lawsuits or PR disasters away from bankruptcy are they? Do they intend to sell to a bigger company who will shut them down?
And most importantly: what would you do if they did?
Being private companies, there is no way to know any of this.
You can take steps to mitigate the risks, like exporting your passwords on a regular basis (which is a good idea anyway) – so that even if they did shut down without notice, you would still be safe – but it’s ultimately up to you to decide whether you (a) believe the companies are telling you the truth about how they store your data; (b) believe they will be around for the long run; (c) are willing to do something like take regular backups (and store them securely – with encryption) to mitigate the risk of (a/b), and decide the potential tradeoffs are worth it for the added convenience.
Closed-Access:
In terms of making sure that you’re the one who is reading your data (at least when it comes to your devices), password managers are nearly top-of-class in terms of the overall.
They (the top ones we’ll be reviewing in this article) allow for all the major current forms of authentication: a master password, support for TouchID/FaceID/Fingerprint Readers on Android/Windows, and even 2FA (which stands for Two-factor authentication/TFA, or multi-factor authentication/MFA – and basically means you use a totally separate app/device as an added layer of security when you log in).
These important authentication practices stop would-be hackers from accessing your passwords if they got a hold of your devices (either physically, or digitally).
However, just like browser-based password storage, there is one major flaw in the standard implementation of these tools from a practical security perspective: automatically filling in forms with your username and password.
Originally, this functionality was (and still is) one of the core selling points of password manager apps – quick, convenient, at-your-fingers logins to all your favorite websites and apps. Yay!
But what happens if somebody gets a hold of your device?
They’ll be saying “Yay!” as well – because they can also log into all of your accounts, and therefore change all your passwords.
While the argument could be made that this type of additional security layer would only be encountered if somebody were to access your already unlocked device, that could happen in many cases, from trojans (a kind of malware that often times gives people uninvited access to your computer remotely, named after its conceptual forebearer from a part of the Ancient Greek myth of the Trojan War), to guessing your device password/PIN, to having your device stolen while logged in, to having the FBI bypass your security (or, apparently anybody with $1500 nowadays).
Now, the companies that make password managers have realized this to be a problem, and created ways to prevent it. It’s important to be aware of this as a potential situation, so that you can decide if the ways to protect yourself from this risk is worth it for the inconvenience they can cause.
Firstly, the automatic login functionality on your computer, comes from the browser plugin/addon/extension itself. If you want to remove the possibility altogether, you can use the Windows/Mac/etc. App, which has the ability to copy and paste your passwords, so you get some of the convenience of password managers (specifically, your passwords all in one place), but lose out on being automatically logged in.
The Apps can be password protected themselves, so when you open them to get your passwords, you have to enter your “master password”; that way, you only need to remember one password. Many of them also integrate with TouchID/FaceID/Fingerprint Readers, so if your computer supports them, you don’t even need to put the master password. Using the password-less login method also protects you from keyloggers (another form of virus, that tracks every key you type), which would render the protection of a master password fairly useless.
Alternatively, some of the better password managers (which we will be recommending) also give you the ability to force the browser plugins/addons/extensions to require you to enter your master password when automatically logging in – either across the board, or only for specific sites – so you don’t have to dig around for individual passwords, while still gaining protection from being automatically logged in.
The problem here – from a standpoint of convenience – is precisely that password managers offer the great feature of logging in without remembering your passwords. Having to enter (and presumably type) a password every time not only leaves you vulnerable to keyloggers – it also takes a step back in convenience, to actually having to manually type something to log in (as we did back in the stone ages).

Until the browser extensions are updated to allow for password-less re-authentication for every login (which the Apps for your phone already support), they are the weak link in the chain, and it’s up to you to decide whether the risk is worth the convenience of automatically logging in.
However, the (relatively) good news is that there are ways around that risk – albeit at the cost of convenience. Hopefully, we’ll soon hear the (absolutely) good news that password-less login options are available universally. That will be a good day for everyday-use, convenient, mass-market password management solutions.
Until then, they still remain an excellent choice as a ready-to-go, plug-n-play password management system, and one truly worth considering if you don’t want to take the time to setup/create your own do-it-yourself password management solution.
Overall:
The Top Password Managers
Before we get into the specific apps, a few points of clarification and disclaimer:
- The nature of software is to improve (or at least iterate/change) over time. These apps may update their features and eliminate their specific shortcomings (and I hope they do). I have watched their evolution for years as I have searched for a fitting password manager app, including testing them at multiple phases in their respective evolutions, and have found many of the shortcomings consistent throughout the years.
- Password management has become a competitive field, with many contenders. I can’t possibly review all of the apps available, and so I focus on the ones that have had longevity (so as to best satisfy the potential concern about how much longer they may be around), and that I see as the most reliable (and in this case, popular), respective to the category.
- Similarly, I am focusing on password managers as they relate to “general usage” – that is, relatively straightforward, day-to-day password needs. There are many different potential needs for password management, and so you may want to look for another solution if you have some exotic and/or particularly complex requirements, such as password sharing (which in and of itself is a questionable practice compared to giving people their own logins).
With that being said, let’s get one major factor out of the way: Price.
If your budget for a password manager that syncs across all your devices is in the $0.00 per ∞ range, then read no further. LastPass is the only one of these which is free to sync across all your devices, and has been since 2016.
Best-in-Class: LastPass
LastPass is also the password manager I recommend for general use-cases. It’s made a lot of progress over the years. From being clunky, buggy, intrusive, annoying, and crashing frequently (although the desktop app still crashes on me in specific scenarios), to being relatively streamlined, while still being full of features, and especially security-focused ones which don’t come at the expense of convenience.
One particularly notable feature in this regard is the nearly ubiquitous ability to use TouchID/FaceID and Fingerprint readers – not only to access your passwords, but even to log in each individual time.
While all the major password managers have the ability to generally or specifically lock logins with a master password, using that functionality still makes you log in each time with your master password – something that nearly nullifies one of the main benefits of having a password manager. On the other hand, having the ability to unlock logins with the same convenience that TouchID/FaceID/Fingerprint scanning brings to unlocking your devices themselves, is a major win for convenience.
It should be noted that the only place that this is not yet possible with LastPass (though they confirmed they are aware of the deficiency), are the browser extensions on Mac, and the dedicated App on Windows. Yes, it works in browsers on Windows, and on the App in Mac, but not the inverse. If you are concerned, you can always use the desktop App, and forgo the automatic logging on for the extra security of always having to enter a TouchID/FaceID/Fingerprint when you access your passwords.
LastPass also has useful functions like an easy-to-access password generation tool, so you can set your preferred password settings (more on that in the “Having Strong Passwords” section) and it generates a new password for you whenever you need it.
It’s also been owned since 2015 by LogMeIn Inc. – a publicly traded company (NASDAQ: LOGM) – so it has about as high an opportunity and as much a probability of being a longevous password management company, as possible.
Second & Third Place: 1Password & Dashlane (Plus RoboForm)
Honorable mentions must be made here to the number 2 and number 3 general purpose password managers – 1Password and Dashlane, respectively.
This isn’t meant to be so much a comparison as a recommendation, but I will briefly summarize that 1Password is a very close contender to LastPass, except:
- Both of them require a subscription to synchronize across multiple devices ($35.88/year for 1Password, $39.96 per year for Dashlane) – not a problem if there is added value, but…
- Comparatively, Dashlane has the fewest features of the 3, and yet is the most expensive (and that’s all that shall be said about it).
- If you want to pay for one, get 1Password, or upgrade to LastPass’s yearly option, which is actually the cheapest of the 3 at only $24 per year – or look into something with some extra features, like RoboForm, which we aren’t covering here, but has some other great features in and of itself (and many more than Dashlane – including deeper integration with TouchID/FaceID/Fingerprints – all at lower cost), but isn’t included in the main lineup because it forces you to use its own browser on Android/iOS; if that’s not a big deal for you, check it out.
As for 1Password:
- I have found that it recognizes significantly fewer forms than LastPass, so sometimes (much more frequently than is convenient), it just won’t capture nor fill in the username/password
- When synchronizing to your phone, I found that quite often, I had to put in my master password, rather than – and even though – I had TouchID enabled for it. Putting in such a long password so frequently on the tiny, inefficient, and inaccurate phone keyboard was a frustration, and time sink.
- The same lack of consistent TouchID integration was also the case for the desktop app, despite their support telling me what the functionality “should” be. Its integration with TouchID just doesn’t seem “finished” (or “ready to ship”).
- The aforementioned is especially a shame given that 1Password used to be the least buggy of the major password managers. Because of this positive history, however, I have hope that they will resolve the bugs at some point soon – but I can’t recommend them in the current (inconsistent) state of affairs.
- On the other hand, if you don’t like/can’t use TouchID/FaceID/Fingerprint sensors anyway, it has an equivalent implementation to LastPass, of either always entering master passwords, or no extra passwords at all – save for the cases when it doesn’t detect the login area (which I found to be the main deal breaker).
- To its credit, 1Password has an interesting feature where it can serve as your 2FA device and automatically paste the 2FA code. Although this somewhat defeats the purpose (2FA stands for 2-Factor Authentication, which means you’re using a second device to verify your account access) by using your password storage service as your 2FA provider (i.e. if they get access to one, they get access to everything, which is what 2FA is designed to prevent) – having it automatically give you the 2FA code is undoubtedly convenient.
While you’re welcome (and encouraged) to research them – and the plethora of others – to find a password manager that suits your needs, I recommend giving LastPass a try first. It’s easy to use, synchronizes across all your devices, has impressive features for both security & convenient, and is free!
Type #3: Do-It-Yourself Password Management
There is, of course, a third category of password management: doing it yourself.
Advice on this category comes in as many forms and angles as there are individual requirements, for what constitutes the need for a custom solution.
From the need to have full control over your data (e.g. due to warranted/unwarranted paranoia being security-minded, facing compliance issues, or advanced access sharing requirements), to complicated login scenarios (I still haven’t found a password manager that can properly differentiate different accounts with the same username over different subdomains/directories of a site) – the use cases can be so highly specialized, with so many potential permutations, that if you truly need a custom solution, I am going to have to assume that either (a) you realize you are going to have to hire a team, or (b) have the technical ability to craft/jerry-rig a solution yourself, and in either case, (c) realize that discussing such a thing is beyond the scope of this article.
None the less, I would be remiss not to at least touch on the existence of the DIY category of password management. From the “sage wisdom” of a password-protected excel sheet, to Apple’s “Secure Notes” (which, despite the name, are not encrypted end-to-end) or iCloud Keychain (which is), to you-name-it – many a cobbled-together solution exist.
Within the realm of do-it-yourself password management, there exist many weeds in which to get lost, and many trees for which to not see the forest (as well as many idioms for which this grammatical structure isn’t exactly suited).
Like What You See?
If you find yourself with a unique set of mandatory criteria for password management, you have some studying to do – and hopefully the criteria I outlined above help in this quest.
If not, then go with a password manager – they are easy to use, fit most common scenarios, and despite the remaining hole of automatic browser-based logins in the case of device theft, remain the most secure (and definitely the most convenient) option for casual use.
The Meta – What’s Always Important
Whether you relegate yourself to the restricted functionality of the built-in password storage of your browser(s), take advantage of the versatility and convenience of a password manager app, or opt to do it all yourself, there are some important principles that it pays to remember – or perhaps more accurately, can be costly to forget.
Having Strong Passwords
The first thing you want to make sure you do, is use strong passwords. In short, that means long passwords (as long as the website will allow) which randomly contain numbers, symbols, and mixed case letters – and a different one for every single service/website/app you sign up for.
Luckily, LastPass has a built-in tool to generate such passwords, whether you use the browser extension or the dedicated app. These tools save your preferred options, so once you have them dialed in, you just open the tool any time you need a strong password (it also integrates directly into account creation forms), and get your fresh password – no work required!
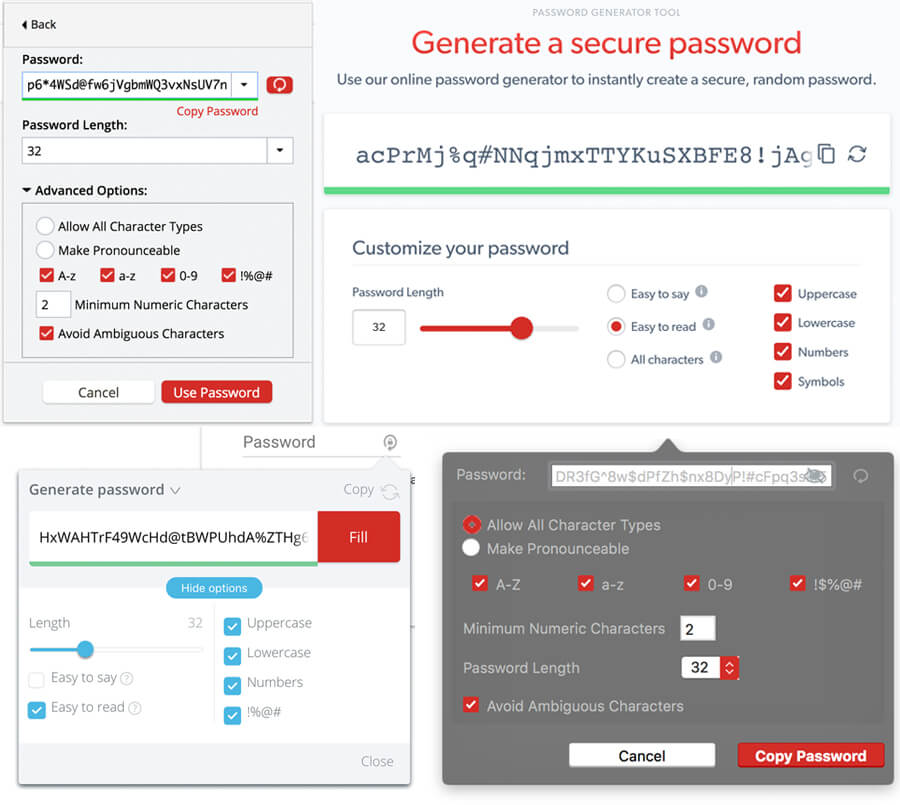
If you don’t use LastPass, you can either mash your keyboard (including alternating the Shift button), or use their online password generator tool with similar settings.
Using Strong Passwords (Practically)
You’ll notice when it comes to length, I have mine set to 32 characters by default. Many more advanced sites these days allow relatively long passwords, and so I like to use 32 as a default. However, they won’t be compatible with all sites – while many have adopted at least a 6 character minimum, some (like banks, unfortunately) still have archaic rules like 6 alphanumeric characters as a maximum.
If you choose to also set your passwords to 32 characters, just know that there are some sites which might not like it. If you get an error message regarding a password (and there is no specific message saying it’s related to length, or symbols, etc.), and you want to use the safest password that site will allow, try these steps, in this order (try it again after each point):
- Reduce the characters to 20
- Reduce the characters to 16
- Send them an angry letter
- Reduce the characters to 12, 10, or finally 8 (6 if you’re dealing with a bank)
- Check to see if the site doesn’t allow symbols in the password, and try again with 20/16 without symbols
If you “are too lazy” don’t prioritize security that much, and would rather not be “inconvenienced” by the extra 30 seconds it might take each time you create an account if you have to change the password length, you can forgo the 32/20 steps and skip right to 16 characters, which is one of the most common password length maximums.
Having & Storing a Strong Master Password
Normal passwords can be long and random, because, whether you’re using a mass-market password manager like LastPass, or some entirely custom solution, you’re not going to have to remember them.
In the case of a password manager, the luxury of no longer needing to remember your passwords is brought to you by virtue of something called a Master Password, which is the key to all your keys. It’s also the concept behind the naming of the industry leader, LastPass – the last password you’ll ever need to remember. Perhaps the same can be said for its top competitor too, 1Password – one password to rule them all (I would assume).
Even if you’re using TouchID/FaceID/Fingerprints to unlock your password manager on a day-to-day basis, you are going to have to come up with & store your master password somewhere. The safest place, is in your head. Perhaps you’ll also store it in a backup somewhere, like an encrypted document, but that begins an endless loop – how will you remember the password for that document?
At some point, if you take shortcuts, you will end up with a weak link. It’s up to you to evaluate in this case whether “security by obscurity” is going to be enough for you. I would argue, that for most people, it would be. If your master password is stored in an encrypted excel sheet, whose password is stored in a Dropbox account linked to a throwaway email address that hasn’t been used anywhere else, and that Dropbox account’s password is in a Secure Note, perhaps that is enough to deter all but the most steadfast hackers/governments (in a security by obscurity kind of way).
But, there is no need to get that complex. In fact, the opposite would be a much better tact: pick a password that’s close to home – but not in the way you’d think.
Years ago, Graham Cluley from Sophos made an excellent video describing how to pick a strong password (the methodology of which often credited to Bruce Scheiener). While he covered password managers at the end, there exists a disjointed logic between the initial recommendation (which is what I am referencing) and the latter portions of the video. Specifically, he describes an excellent way of coming up with a password that is memorable to you:
1. Pick a phrase that has meaning to you – better if it’s simple
2. Take the first letter of each word as the base for your password
3. Make a small number of substitutions (e.g. a symbol and a number) – the point being, not too many for you to forget
4. Capitalize the first one (and perhaps proper nouns)
5. There’s your password
Here’s an example, with bolding/underline added for emphasis:
1. Do you remember that night, the sky so bright, last July?
2. dyrtntssblj? (We are skipping commas for the sake of memorization, but including the question mark, both for additional entropy, and as a potential reminder)
3. dyr7n7$$blj? (Notice that both t’s and both s’s have been replaced with numbers/symbols that look similar – so I just remember that I replaced both of them, rather than guessing which it was)
4. Dyr7n7$$blJ?
5. There it is!
When we run it through an entropy calculator, we see that in a worst-case scenario (worst for you, best for a potential hacker – meaning a scenario in which they hacked the service and had access to the raw data, and has multiple high-powered computers each with multiple high-powered graphics cards dedicated to the task), it would take 174 years to crack the password with 100% certainty (highlighted in red).
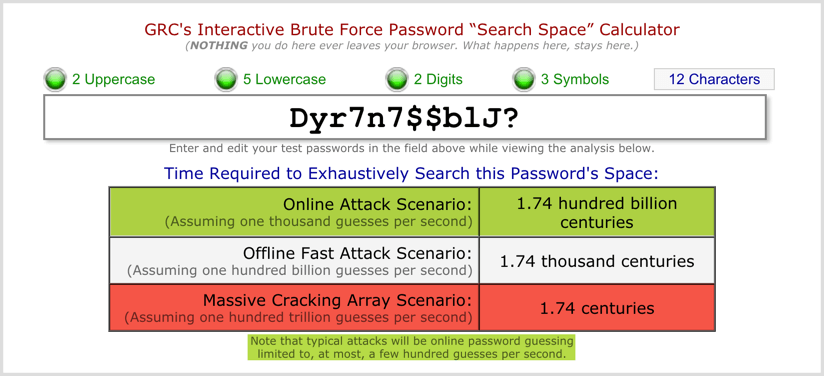
In a much more probable situation (highlighted in green), in which a potential hacker tries to access your account by automated password entry on a web form, he will get your password with 100% certainty about 1,732,500,000,000 years after the sun engulfs the Earth.
It should be disclaimed that these numbers indicate how long it would take to guarantee your password will be cracked, by virtue of literally every password being attempted; although extremely likely, your password could be the first one that is attempted, or the hundredth (meaning it would be over in less than a second) – however, the likelihood of this happening, is what we are reducing by adding more entropy (longer, upper/lower case, digits, symbols), because more than likely, the first hundred passwords that will be attempted are the low hanging fruit.
In the video, he references this as a way to create every single password you have, but with randomized password generators, and no need to remember the majority of your passwords, you don’t have to go through this process every time – just for the master password.
Now, there is varying thought on what makes a strong, memorable password. The above is one strategy, but does take some time to commit to memory, and due to its pedantic nature, may be forgotten, which is why it is especially helpful (though ALWAYS a good idea) to have it stored somewhere securely, without getting into the aforementioned crux of security by obscurity – partly because you then also have to remember how you have the whole thing setup.
Another popular method – and one without which no password guide would be complete, is to use a randomized phrase as your password (courtesy of xkcd):
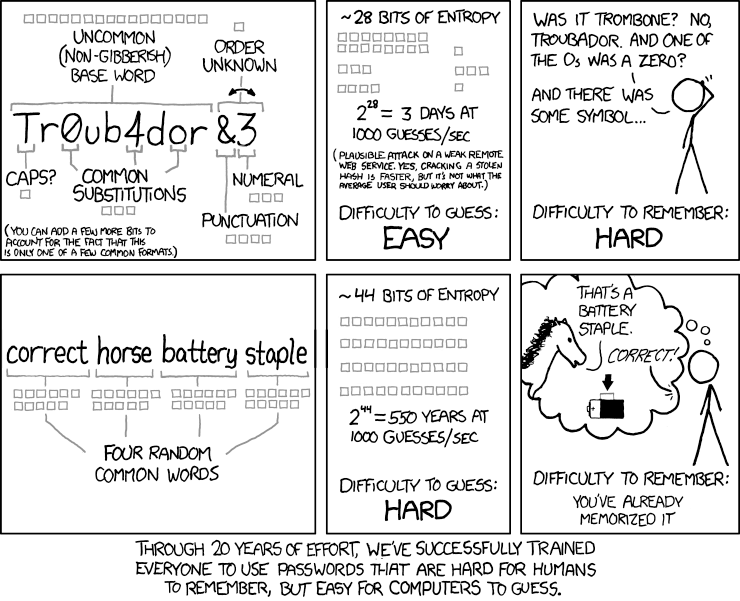
The key here is length, and memorability. The longer the better (since LastPass has no master password limit), as long as you can memorize it – which may be easier than you think.
Again, there is plenty of debate to be had about the efficacy of password strategies, with everybody and their brother’s sister’s daughter’s pediatrician having an opinion.
The above two methods (among plenty of others) are the ones I find to be the easiest to remember, while still providing enough entropy to keep it safe for all practical intents and purposes.
Pick the one that you think you’ll be most likely to remember, make it long (12 characters was an example, and pretty short at that), then spend a bit of time memorizing it. If using a password manager, you can enable the master password-based re-authentication features to start (and keep them enabled for browser-based logins), so you get some practice entering it on a regular basis.
Conclusion
Ultimately, the best password storage solution is the one you actually use. If you know your desire for convenience is greater than the relatively small amount of effort it takes to copy and paste passwords across devices, then use a password manager, backup your data from time to time, and either use your master password (or TouchID/FaceID/Fingerprint where applicable) to log in every time, or hope nobody malicious gets access to your devices.
At the very least, doing so will make it easier and faster to automatically log in to most, if not all of your online accounts, without having to remember passwords (and therefore never having to worry about forgetting them).
In that case, you only ever have to remember one password (make sure to keep it strong), and you won’t even have to use that to access to your logins day-to-day if you have TouchID/FaceID, or a fingerprint scanner on your Android phone or Windows computer.
When it comes to the password manager of choice, if you don’t want to pay to be able to access your passwords across all your devices, get LastPass, as it’s the only one that syncs across your devices for free. It also happens to have a useful feature set, as well as many configuration settings, both of which are security and convenience-oriented. It’s easy to use, and great for those with generally straightforward day-to-day password storage needs.
If you’re looking for an alternative, you can try 1Password, or Dashlane/Roboform – but whatever you do, don’t rely on your browser’s password storage system.
Finally, do something.
Security is often an after-thought, because “if it ain’t broke, don’t fix it”, right?
But what does broke mean – do you know?
Does broke mean that it just doesn’t bother you much day-to-day, and you can get by, or does broke mean that you actually know what you would do – how you would get back into your email, your social media, online banking, and all your other accounts – if all your devices were suddenly lost or stolen?
Think about it for a second. If you would be in deep doo doo, then decide to invest the hour or two it takes to setup a password manager, and protect your digital life from the potential perils of travel.
